Mastering User and Access Management with LogiNext
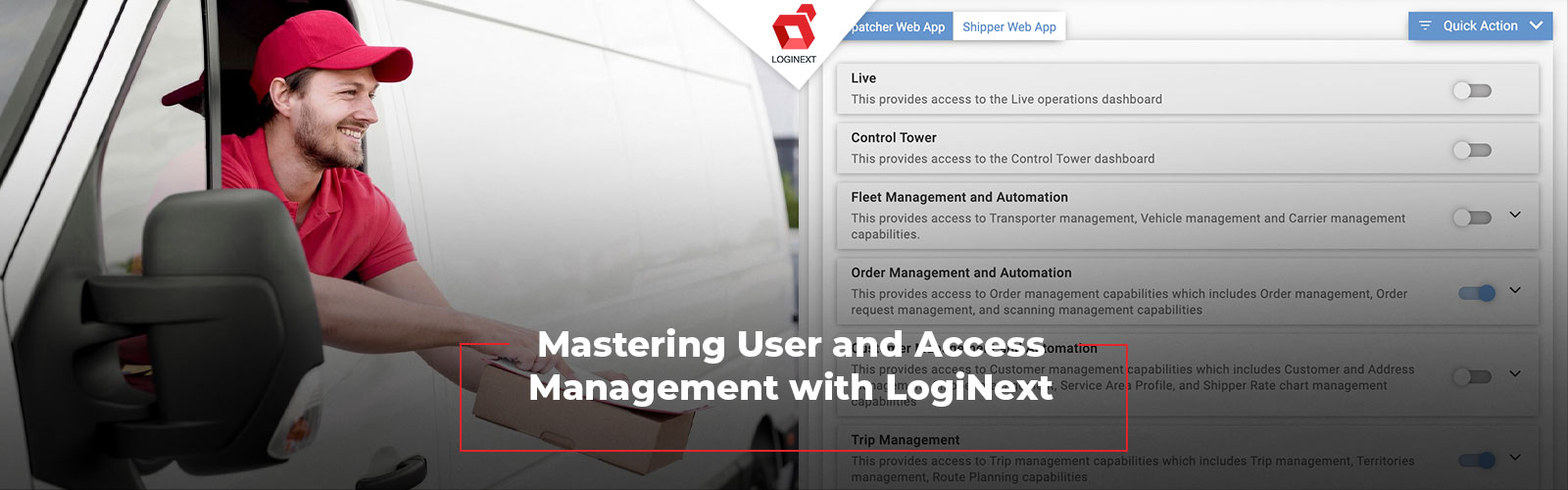
Managing access in a logistics organization is a balancing act between security, efficiency and usability. As logistics operations grow more complex, with teams handling diverse roles and responsibilities, a robust access management system becomes essential. LogiNext’s user and access management module is designed to address the need, providing businesses with intuitive tools to assign, refine and manage access levels across teams.
By using LogiNext’s user and access management solution, you can ensure your operations remain secure, efficient and scalable. Let’s explore how this system is structured and why it’s an indispensable part of modern logistics management.
The Three Pillars of User and Access Management
LogiNext’s user and access management framework rests on three core components: Users, Organization Roles, and Access Profiles. Together, these elements create a structured yet flexible system for controlling access to features, data, and capabilities.
Users: The Foundation of the System
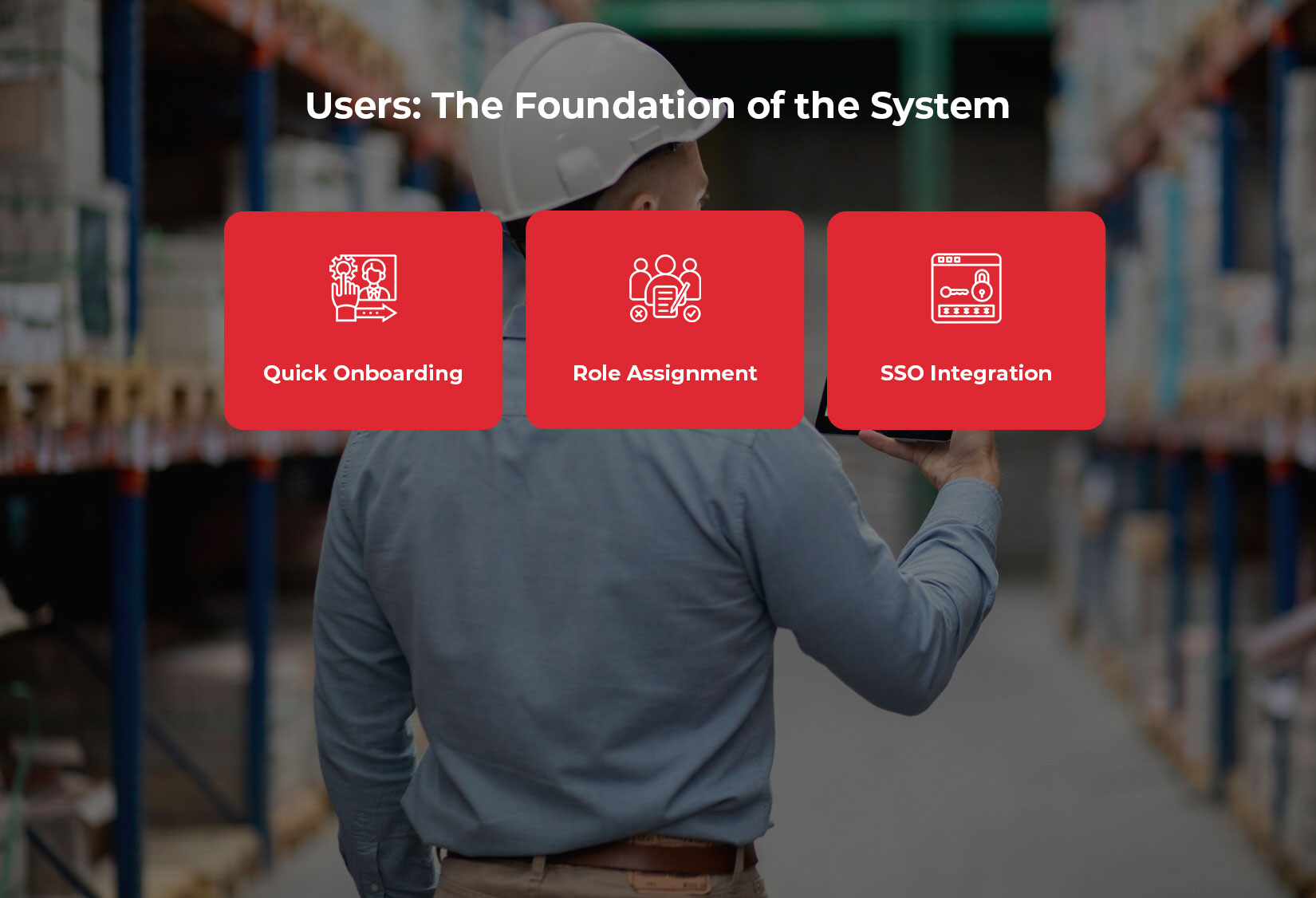
At the heart of the system are users—the individuals who interact with the LogiNext platform. Each user has unique responsibilities and access needs. Here’s how LogiNext makes user management straightforward:
1. Quick Onboarding:
Administrators can easily add users, ensuring they have immediate access to the tools and features needed for their roles. This ensures a seamless start for new users.
2. Role Assignment:
When creating a user profile, administrators assign a predefined organization role that defines the user’s scope within the system. As responsibilities evolve, these roles can be updated, ensuring the user’s access always aligns with their current responsibilities.
3. SSO Integration:
For added security and convenience, users can log in through Single Sign-On (SSO), eliminating the need to manage multiple credentials.
By combining these features, LogiNext ensures that user management is both secure and practical, while also addressing the unique needs of every individual.
Organization Roles: Defining Responsibilities

Organization roles outline the scope of access and responsibilities for different types of users. In doing so, these roles bring clarity and structure to your system. With LogiNext’s organization roles, you get:
1. Persona-based Roles:
Roles are designed around common user personas like dispatchers, shippers, or carriers. For instance, dispatchers handle route planning and assignments, while carriers focus on transportation tasks. This ensures that access remains relevant and efficient.
2. Branch-Level Customization:
Roles can be tailored to specific locations or operations. For example, a dispatcher in New York can have the same role as one in Boston but with region-specific access.
3. Customized Landing Pages:
Administrators can set a default landing page for each role, directing users to the dashboard or tools most relevant to them.
4. Adaptability:
Organizations can adjust roles to reflect new workflows or responsibilities as their needs evolve.
By clearly defining roles, LogiNext eliminates confusion, enhances accountability, and ensures each team member has the tools they need.
Access Profiles: Fine-Tuning Permissions

Access profiles build on the structure provided by organization roles, offering even greater control over what users can do and see. Here’s how access profiles work:
1. Permission Bundles:
Instead of assigning permissions one by one, administrators create profiles that bundle related permissions. For example, a “Route Optimization” profile might include access to route planning tools, analytics, and scheduling features.
2. Granular Control:
You can set permissions at multiple levels, such as menus, pages, buttons, and fields. As a result, this precision ensures users only interact with what’s necessary for their role.
3. Flexible Linkages:
Organization roles can have multiple access profiles, and a single access profile can serve multiple roles. This means that configurations can adapt to your business needs.
4. Pre-Configured Profiles:
LogiNext offers ready-to-use profiles for common use cases, making setup quick and easy. Additionally, individuals can customize these profiles to suit specific requirements.
Access profiles ensure that permissions are consistent, scalable, and easy to manage—forming the bridge between organization roles and actionable capabilities.
How It All Works Together
The interplay between users, organization roles and access profiles is what makes LogiNext’s system so effective. Specifically, administrators assign users to roles and these roles link to access profiles that define which features and data the users can access. As a result, this hierarchical structure keeps everything clear, consistent and secure.
For example, when a new dispatcher joins the New York team, they can be assigned the “Dispatcher” role during onboarding. Consequently, this role comes with pre-configured access profiles for dispatch-related tasks, giving them the tools they need from day one while simultaneously restricting access to unrelated or sensitive information.
A Critical Layer: Security
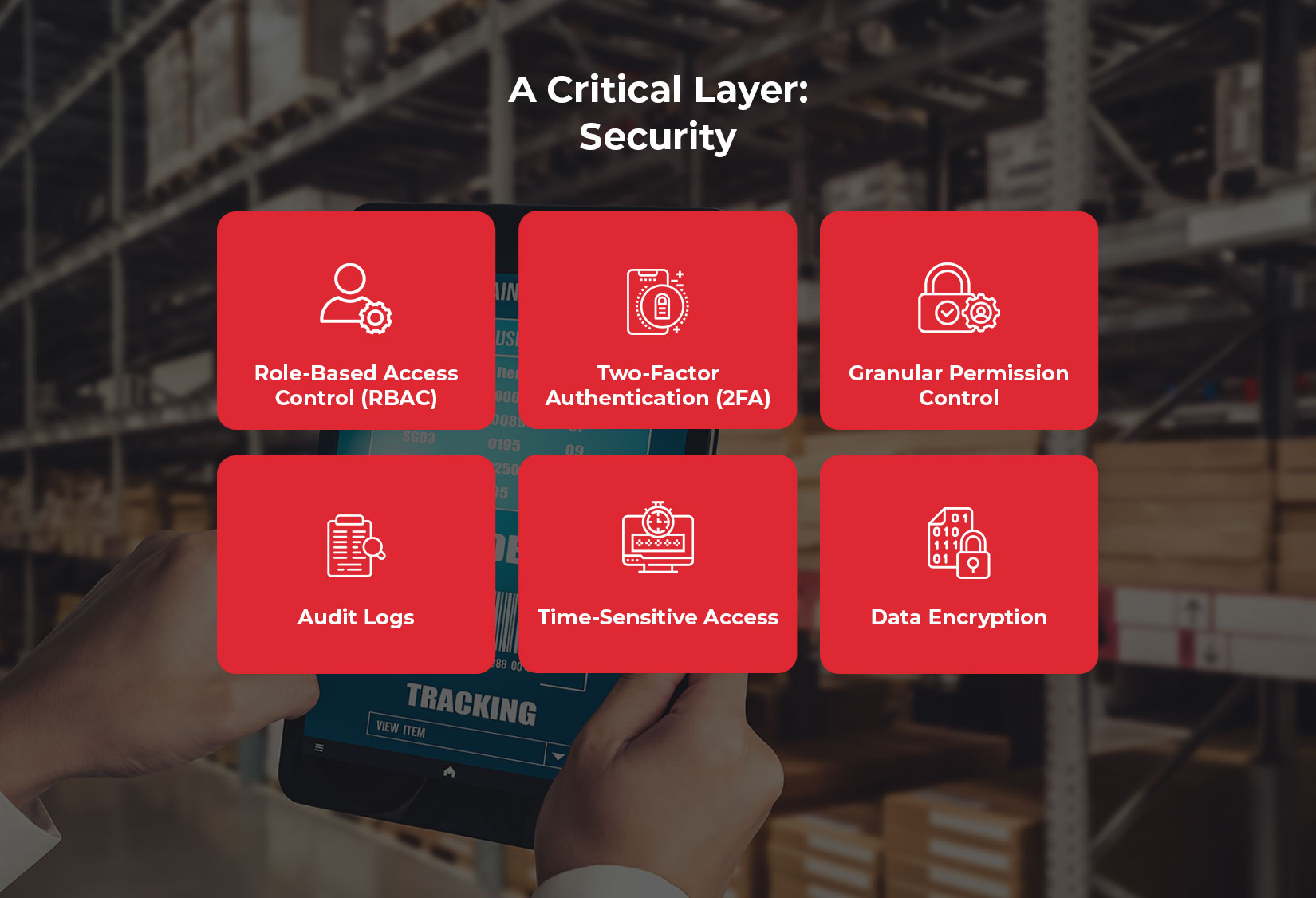
Access management is not just about assigning roles—it’s a cornerstone of protecting sensitive data, ensuring compliance, and safeguarding operations from internal and external threats. Therefore, LogiNext integrates robust security measures to provide a comprehensive defense framework.
– Role-Based Access Control (RBAC): Users can only access the tools, data, and features relevant to their roles, thereby minimizing exposure to sensitive information.
– Two-Factor Authentication (2FA): This measure adds an additional layer of security by requiring users to verify their identity beyond a password.
– Granular Permission Control: Permissions can be tailored down to specific fields, buttons, or actions, thus ensuring precision in access.
– Audit Logs: Comprehensive logs track every access attempt and action, enabling full transparency and simplifying compliance report.
– Time-Sensitive Access: Temporary permissions for contractors or special projects enhance security while also maintaining operational flexibility.
– Data Encryption: All sensitive data is encrypted, both at rest and in transit, thereby preventing unauthorized access.
Together, these measures not only protect your business from data breaches but also foster trust with clients by ensuring responsible handling of their information.
Built for Ease and Scalability
LogiNext knows that businesses need solutions that are both powerful and easy to implement. That’s why the platform includes pre-configured organization roles and access profiles—so you can get started quickly. Moreover, as your business evolves, the system’s flexibility ensures you can adapt roles and profiles to meet changing needs.
By combining intuitive user management with robust access controls, LogiNext enables businesses to secure their operations and improve efficiency. Consequently, with this system in place, you can focus on what matters most: delivering exceptional service to your customers.
Conclusion: Empower Your Team with LogiNext
Access management isn’t just a technical feature; instead, it’s a critical driver of efficiency, security, and scalability. With LogiNext’s User and Access Management module, you’ll have the confidence that every user has the right tools and permissions to succeed.
Whether you’re a growing startup or a well-established enterprise, LogiNext provides the foundation for streamlined, secure operations. Therefore, say goodbye to complexity and security risks. Say hello to a more empowered, efficient team. Book a demo with us today!
54







@LogiNext