
Cybersecurity in TMS: Protecting Logistics Data
In the modern logistics landscape, technology drives efficiency, transparency, and scalability. Among the critical tools that power supply chains is transportation management software (TMS). However, as TMS solutions become more integrated into global operations, they are increasingly exposed to cybersecurity risks. Safeguarding logistics data is no longer optional; it is essential for the seamless functioning of supply chains.
The Role of Transportation Management Software in Logistics
Transportation management software plays a pivotal role in streamlining logistics processes. From route optimization and freight auditing to real-time shipment tracking, TMS systems ensure operational efficiency. Companies adopting the best transportation management software can witness improved delivery timelines, reduced costs, and enhanced customer satisfaction. Yet, with the increasing dependence on digital platforms comes the pressing need to secure sensitive logistics data from cyber threats.
Rising Cybersecurity Threats in TMS
TMS platforms handle vast amounts of data, including customer details, freight information, payment transactions, and supplier contracts. Unfortunately, this data is a lucrative target for cybercriminals. By 2025, cybercrime damages are predicted to exceed $10.5 trillion yearly, per an estimate by Cybersecurity Ventures. For logistics companies relying on transportation management solutions, a breach could lead to financial loss, reputational damage, and legal implications.
Common Cybersecurity Risks for TMS

1. Data Breaches:
Unauthorized access to sensitive data can disrupt operations and erode customer trust. Hackers may exploit weak passwords, outdated software, or unsecured networks to infiltrate systems. Once inside, they can steal, manipulate, or sell critical information.
2. Ransomware Attacks:
Malicious software can lock access to critical TMS systems, halting operations until a ransom is paid. These attacks have become increasingly sophisticated, targeting vulnerabilities in software or exploiting human errors to gain entry.
3. Phishing Scams:
Targeted attacks that trick employees into revealing login credentials can compromise entire systems. Phishing emails often appear legitimate, making them a common and effective tactic for gaining unauthorized access.
4. Third-Party Vulnerabilities:
TMS solutions often integrate with third-party platforms, creating potential entry points for cybercriminals. Weak security measures in these integrations can allow attackers to access the entire network.
5. Insider Threats:
Disgruntled employees or contractors with access to TMS platforms can intentionally or unintentionally compromise data security. Without proper monitoring, these threats can go undetected.
Strategies for Protecting Logistics Data in TMS
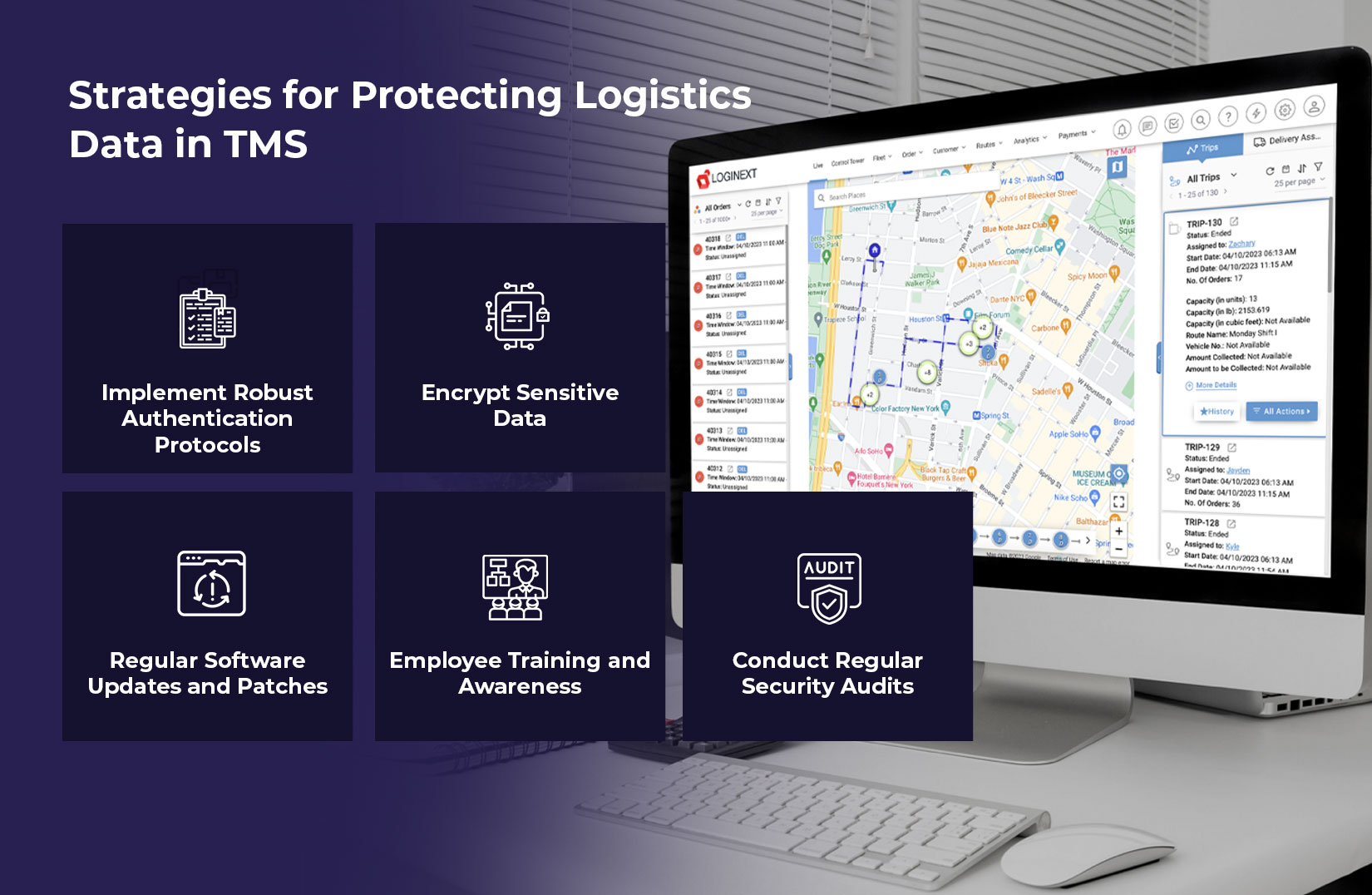
1. Implement Robust Authentication Protocols:
Multi-factor authentication (MFA) adds an extra layer of security to TMS platforms. Requiring users to verify their identity through multiple channels can significantly reduce unauthorized access. According to Microsoft, MFA can block over 99.9% of account compromise attacks.
2. Encrypt Sensitive Data:
Even if data is intercepted, encryption makes sure that it cannot be decrypted without the right key. This is especially crucial for payment and customer information handled by transportation management software. Statista reports that over 60% of companies now prioritize encryption to safeguard sensitive information.
3. Regular Software Updates and Patches:
Outdated software is a prime target for cyberattacks. Regular updates and patches for your transportation management solution can close security gaps and protect against known vulnerabilities. Research shows that nearly 60% of data breaches are linked to unpatched software.
4. Employee Training and Awareness:
One of the main reasons for cybersecurity vulnerabilities is human mistake. Training employees on recognizing phishing attempts and practicing safe online behaviors can mitigate risks. A study by IBM found that 95% of cybersecurity breaches are primarily caused by human error.
5. Conduct Regular Security Audits:
Frequent audits of TMS systems help identify potential vulnerabilities. These audits should include testing third-party integrations to ensure they meet security standards. According to the Ponemon Institute, companies that conduct regular audits save an average of $1.23 million per breach.
Future Trends in Cybersecurity for TMS
1. AI- Driven Threat Detection:
Artificial intelligence is increasingly used to detect and respond to threats in real time. AI-powered tools can monitor TMS platforms for unusual activity and neutralize potential breaches. Gartner predicts that by 2025, over 50% of cybersecurity operations will rely on AI to enhance detection accuracy and speed.
2. Blockchain Technology:
Blockchain offers a decentralized method of securing logistics data, ensuring transparency and preventing unauthorized alterations. By creating an immutable ledger of transactions, blockchain reduces the risk of data tampering. A PwC report highlights that 84% of companies are exploring blockchain for improved security in supply chain processes.
3. Zero Trust Architecture:
This method makes the assumption that no device or user is reliable by default. Zero Trust ensures continuous verification of every access request within the TMS. As reported by Forrester, organizations implementing Zero Trust models experience a 50% reduction in the risk of breaches caused by insider threats.
4. Advanced Threat Intelligence:
Integrating global threat intelligence feeds into TMS platforms enables proactive defense against emerging threats. Threat intelligence provides real-time updates on cyber risks, allowing companies to fortify their systems before an attack occurs. The global threat intelligence market is projected to grow at a CAGR of 17.9%, reflecting its importance in modern cybersecurity.
5. Integration of IoT Security:
The growing use of IoT devices in logistics, such as GPS trackers and smart sensors, creates new vulnerabilities. Future TMS solutions will prioritize IoT security, monitoring and securing these devices against potential exploits. According to Statista, there will be over 75 billion connected IoT devices by 2025. This underscores the need for robust IoT integration strategies.
Also Read: Blue Yonder’s Security Fails: LogiNext is the Right Solution
Conclusion
As the logistics industry embraces digital transformation, safeguarding sensitive data becomes paramount. By leveraging secure transportation management solutions and implementing proactive cybersecurity measures, companies can protect their operations and maintain trust. Investing in the best transportation management software with strong security protocols is not just a technological upgrade. It is also a strategic necessity for long-term success.
In a world where cyber threats are evolving, staying ahead requires vigilance, innovation, and a commitment to cybersecurity. Prioritize the protection of your transportation management system today to safeguard your logistics data for tomorrow. Click on the red button below to get the best system with the best cybersecurity in today’s market. Book a demo with LogiNext solutions and protect your future today.
45







@LogiNext